So far I have written a couple of posts in which I dive into the code for the ASP.NET Core 1.0 Identity library. In this post I want to do something a little more practical and look at extending the default identity functionality. I’m working on a project at the moment which will be very reliant on a strong user management system. As I move forward with that and build up the requirements I will need to handle things not currently available in the Identity library. Something missing from the current Identity library is user security auditing, an important feature for many real world applications where compliance auditors may expect such information to be available.
Before going further, please note that this code is not final, production ready code. At this stage I want to prove my concept and meet some initial requirements that I have. I expect I’ll end up extending and refactoring this code as my project develops. Also, at the time of writing ASP.NET Core 1.0 is at release candidate 1. We can expect some changes in RC2 and RTM which may require this code to be adjusted. Feel free to do so, but copy and paste at your own risk!
At this stage in my project, my immediate requirement is to store successful login, failed login and logout events in an audit table within my database. I would like to collect the visitor IP address also. This data might be useful after some kind of security breach; for example to review who was logged into the system as well as where from. It would also allow for some analysis of who is using the application and how often / at what times of day. Such data may prove useful to plan upgrades or to encourage more use of the application. Remember that if you record this information, particularly within a public facing SaaS style application, you may well need to include details of what you’re data recording and why, in your privacy policy.
I could implement this auditing functionality within my controllers. For example I could update the Login action on the Account controller to write into an audit table directly. However I don’t really like that solution. If anyone implements a new controller/action to handle login or logout then they would need to remember to also add code to update the audit records. It makes the Login action method more responsible than it should be for performing the audit logic, when really this belongs deeper in the application.
If we take a look at the Login action on the Account controller we can see that it calls into an instance of a SignInManager. In a default MVC application this is setup in the dependency injection container by the call to AddIdentity within the Startup.cs class. The SignInManager provides the default implementations of sign in and sign out logic. Therefore this is a better candidate in which to override some of those methods to include my additional auditing code. This way, any calls to the sign in manager, from any controller/action will run my custom auditing code. If I need to change or extend my audit logic I can do so in a single class which is ultimately responsible for handling that activity.
Before doing anything with the SignInManager I needed to define a database model to store my audit records. I added a UserAudit class which defines the columns I want to store:
public class UserAudit
{
[Key]
public int UserAuditId { get; private set; }
[Required]
public string UserId { get; private set; }
[Required]
public DateTimeOffset Timestamp { get; private set; } = DateTime.UtcNow;
[Required]
public UserAuditEventType AuditEvent { get; set; }
public string IpAddress { get; private set; }
public static UserAudit CreateAuditEvent(string userId, UserAuditEventType auditEventType, string ipAddress)
{
return new UserAudit { UserId = userId, AuditEvent = auditEventType, IpAddress = ipAddress };
}
}
public enum UserAuditEventType
{
Login = 1,
FailedLogin = 2,
LogOut = 3
}
In this class I’ve defined an Id column (which will be the primary key for the record), a column which will store the user Id string, a column to store the date and time of the audit event, a column for the UserAuditEventType which is an enum of the 3 available events I will be auditing and finally a column to store the user’s IP address. Note that I’ve made the UserAuditId a basic auto-generated integer for simplicity in this post, however in my final code I’m very likely going to use fluent mappings to make a composite primary key based on user id and the timestamp instead.
I’ve also included a static method within the class which creates a new audit event record by taking in the user id, event type and the ip address. For a class like this I prefer this approach versus exposing the property setters publically.
Now that I have a class which represents the database table I can add it to the entity framework DbContext:
public class ApplicationDbContext : IdentityDbContext<ApplicationUser>
{
public DbSet<UserAudit> UserAuditEvents { get; set; }
}
At this point, I have a new table defined in code which needs to be physically created in my database. I will do this by creating a migration and applying it to the database. As of ASP.NET Core 1.0 RC1 this can be done by opening a command prompt from my project directory and then running the following two commands:
dnx ef migrations add “UserAuditTable”
dnx ef database update
This creates a migration which will create the table within my database and then runs the migration against the database to actually create it. This leaves me ready to implement the logic which will create audit records in that new table. My first job is to create my own SignInManager which inherits from the default SignInManager. Here’s what that class looks like before we extend the functionality:
public class AuditableSignInManager<TUser> : SignInManager<TUser> where TUser : class
{
public AuditableSignInManager(UserManager<TUser> userManager, IHttpContextAccessor contextAccessor, IUserClaimsPrincipalFactory<TUser> claimsFactory, IOptions<IdentityOptions> optionsAccessor, ILogger<SignInManager<TUser>> logger)
: base(userManager, contextAccessor, claimsFactory, optionsAccessor, logger)
{
}
}
I define my own class with it’s constructor inheriting from the base SignInManager class. This class is generic and requires the type representing the user to be provided. I also have to implement a constructor, accepting the components which the original SignInManager needs to be able to function. I pass these objects into the base constructor.
Before I implement the logic and override some of the SignInManager’s methods I need to register this custom SignInManager class with the dependency injection framework. After checking out a few sources I found that I could simply register this after the AddIdentity services extension in my StartUp.cs class. This will then replace the SignInManager previously registered by the Identity library.
Here’s what my ConfigureServices method looks like with this code added:
public void ConfigureServices(IServiceCollection services)
{
// Add framework services.
services.AddEntityFramework()
.AddSqlServer()
.AddDbContext<ApplicationDbContext>(options =>
options.UseSqlServer(Configuration["Data:DefaultConnection:ConnectionString"]));
services.AddIdentity<ApplicationUser, IdentityRole>()
.AddEntityFrameworkStores<ApplicationDbContext>()
.AddDefaultTokenProviders()
.AddUserManager<AuditableUserManager<ApplicationUser>>();
services.AddScoped<SignInManager<ApplicationUser>, AuditableSignInManager<ApplicationUser>>();
services.AddMvc();
// Add application services.
services.AddTransient<IEmailSender, AuthMessageSender>();
services.AddTransient<ISmsSender, AuthMessageSender>();
}
The important line is services.AddScoped<SignInManager<ApplicationUser>, AuditableSignInManager<ApplicationUser>>(); where I specificy that whenever a class requires a SignInManager<ApplicationUser> the DI container will return our custom AuditableSignInManager<ApplicationUser> class. This is where dependency injection really makes life easier as I don’t have to update multiple classes with concreate instances of the SignInManager. This one change in my startup.cs file will ensure that all dependant classes get my custom SignnManager.
Going back to my AuditableSignInManager I can now make some changes to implement the auditing logic I require.
public class AuditableSignInManager<TUser> : SignInManager<TUser> where TUser : class
{
private readonly UserManager<TUser> _userManager;
private readonly ApplicationDbContext _db;
private readonly IHttpContextAccessor _contextAccessor;
public AuditableSignInManager(UserManager<TUser> userManager, IHttpContextAccessor contextAccessor, IUserClaimsPrincipalFactory<TUser> claimsFactory, IOptions<IdentityOptions> optionsAccessor, ILogger<SignInManager<TUser>> logger, ApplicationDbContext dbContext)
: base(userManager, contextAccessor, claimsFactory, optionsAccessor, logger)
{
if (userManager == null)
throw new ArgumentNullException(nameof(userManager));
if (dbContext == null)
throw new ArgumentNullException(nameof(dbContext));
if (contextAccessor == null)
throw new ArgumentNullException(nameof(contextAccessor));
_userManager = userManager;
_contextAccessor = contextAccessor;
_db = dbContext;
}
public override async Task<SignInResult> PasswordSignInAsync(TUser user, string password, bool isPersistent, bool lockoutOnFailure)
{
var result = await base.PasswordSignInAsync(user, password, isPersistent, lockoutOnFailure);
var appUser = user as IdentityUser;
if (appUser != null) // We can only log an audit record if we can access the user object and it's ID
{
var ip = _contextAccessor.HttpContext.Connection.RemoteIpAddress.ToString();
UserAudit auditRecord = null;
switch (result.ToString())
{
case "Succeeded":
auditRecord = UserAudit.CreateAuditEvent(appUser.Id, UserAuditEventType.Login, ip);
break;
case "Failed":
auditRecord = UserAudit.CreateAuditEvent(appUser.Id, UserAuditEventType.FailedLogin, ip);
break;
}
if (auditRecord != null)
{
_db.UserAuditEvents.Add(auditRecord);
await _db.SaveChangesAsync();
}
}
return result;
}
public override async Task SignOutAsync()
{
await base.SignOutAsync();
var user = await _userManager.FindByIdAsync(_contextAccessor.HttpContext.User.GetUserId()) as IdentityUser;
if (user != null)
{
var ip = _contextAccessor.HttpContext.Connection.RemoteIpAddress.ToString();
var auditRecord = UserAudit.CreateAuditEvent(user.Id, UserAuditEventType.LogOut, ip);
_db.UserAuditEvents.Add(auditRecord);
await _db.SaveChangesAsync();
}
}
}
Let’s step through the changes.
Firstly I specify in the constructor that I will require an instance of the ApplicationDbContext, since we’ll directly need to work with the database to add audit records. Again, constructor injection makes this nice and simple as I can rely on the DI container to supply the appropriate object at runtime.
I’ve also added some private fields to store some of the objects the class receives when it is constructed. I need to access the UserManager, DbContext and IHttpContextAccessor objects in my overrides.
The default SignInManager defines it’s public methods as virtual, which means that since I’ve inherited from it, I can now supply overrides for those methods. I do exactly that to implement my auditing logic. The first method I override is the PasswordSignInAsync method, keeping the signature the same as the original base method. I await and store the result of the base implementation which will actually perform the sign in logic. The base method returns a SignInResult object with the result of the sign in attempt. Now that I have this result I can use that to perform some audit logging.
I cast the user object to an IdentityUser so that I can access it’s ID property. Assuming this cast succeeds I can go ahead and log an audit event. I get the remote IP from the context, then I inspect the result and call it’s ToString method(). I use a switch statement to generate an appropriate call to the CreateAuditEvent method passing in the correct UserAuditEventType. If a UserAudit object has been created I then write it into the database via the DbContext that was injected into this class when it was constructed.
I have a very similar override for the SignOutAsync method as well. In this case though I have to get the user via the HttpContext and use the UserManager to get the IdentityUser based on their user id. I can then write a logout audit record into the database. Running my application at this stage and performing some logins, login attempts with an incorrect password and logging out I can check my database and see some records being stored in the database.
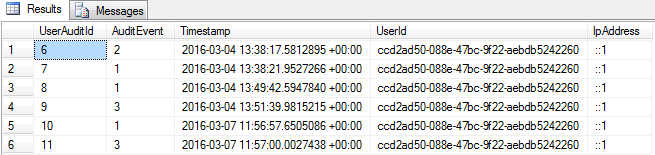
Summing Up
Whilst not yet fully featured, this blog post hopefully demonstrates the initial steps that we can follow to quite easily extend and override the ASP.NET Core Identity SignInManager class with our own implementation. I expect to be refactoring and extending this code further as my requirements determine.
For example, while the correct place to call the auditing logic is from the SignInManager, I will likely create an AuditManager class which should have the responsibility to actually create and write the audit records. If I do this then I will still need my overridden SignInManager class which would require an injected instance of the AuditManager. As my audit needs grow, so will my AuditManager class and some code will likely get reused within that class.
Including an extra class at this stage would have made this post a bit more complex and have taken me away from my initial goal of showing how we can extend the functionality of the SignInManager class. I hope that this post and the code samples prove useful to others looking to do similar extensions to the default behaviour.
Have you enjoyed this post and found it useful? If so, please consider supporting me:

Hi Steve, really interesting post.
With regards to the following code with appears in your article:
> “.AddUserManager<AuditableUserManager>();”
Do you have any code samples for who you have implemented your “AuditableUserManager” ??
Thanks in advance, X22
Hi. I’m glad you found it interesting. The AuditableUserManager is just a stub at this stage and I do have plans to explore extending that as well. The end goal will be to record audit records of user creation events and other similar actions. I’ve not dug into it yet but it does seem that with that AddUserManager method you can pass in your own implementation of the class. I do plan to explore it further and will put up a post about it. For now I’ve been working to making the AuditableSignInManager into a more fully featured piece of reusable code.
I’m getting a weird issue where my User manager is getting disposed prematurely during 2FA verification.
I only solved it by making my AuditableSignInManager a singleton.
Any ideas?
Great article Steve, thanks for sharing it, I was trying to upgrade my custom identity from the previous .net but unfortunately I was not able to achieve it because the password provider that Im currently using is DESCryptoProvider and I realize that this provider does not exist for asp.net core, any ideas about how can I use it or replace it on asp.net core?
Thanks In Advance
Thanks Camilo. You’re welcome. I’m afraid offhand I’m not sure. I know some of the encryption libraries have had to be amended in .NET Core to support cross platform.
looks like an update to the userManager in the signoutAsync method.
line 61
var user = await _userManager.FindByIdAsync(_contextAccessor.HttpContext.User.GetUserId()) as IdentityUser;
should now be:
var user = await _userManager.GetUserAsync(_contextAccessor.HttpContext.User) as IdentityUser;
https://docs.microsoft.com/en-us/aspnet/core/migration/rc1-to-rtm#identity
Hi there,
I was wondering how you handle the case where a user uses “Remember me” option? Technically they are not logging in so how would log these users?
Great article,
I was wondering how you are handling the Audit for when someone has the “Remember Me” option set. Technically they are not logging in so my understanding is that you won’t be capturing those people?
Do you have an example of how to add this custom SignInManager to a ASP.NET Identity project?
The code that shows how the ApplicationSignInManager is added, uses a callback and I’m not sure where to put the custom SignInManager.
Hi Karsten. This is quite an old post now so things may have changed a little, but you should just be able to register the custom SignInManager in the ConfigureServices so that it’s used instead of the default SignInManager where ever that gets injected. Then you should have to change little else.
Hello,
I was wondering if you could guide me or point me in any direction. I am not using any database or in memory users or clients to sign in users. Right now I am using an API to to check the user account, at least I am trying to do that. But I cannot seem to log in the user actually after validating him through the API. Also, I do not want to retrieve all the users with their passwords to check if the user name and password are validated. Could you help with any ideas?
Thank you
Make sure to call base.SignInOrTwoFactorAsync() or base.SignIn() after doing your custom validation. The Identity sub-system will setup the needed things (like cookies or headers) on the HTTP context to make sure your user shows up as being signed in.
Hi Steve,
What a very informative article ! Thanks a lot for taking the time to explain this subject properly.
I hope you can send some help or guidance with an issue that I am completely stuck with:
I am using an Angular 2 front end app and super light Web Api 2 services (without any MVC views or controllers) on top of ASP.NET Core (latest version) and Asp.NET Identity Core.
Everything works flawlessly (verify email and reset password tokens), both in my local dev machine and the server, but *only when the App Pool has not been recycled*.
Every single time the App Pool is recycled in IIS, I cannot validate user tokens anymore (e.g. EmailConfirmationToken). At the beginning I thought that it was related to time zones (remote users started giving me the problem) or token encoding (eastern europe for example).
But then I read somewhere that every time that you create a new instance of the UserManager class, it will use internally some sort of in-memory properties to generate the token.
Since I never used any session data on my services, I could not believe this could happen, because everything should be happening in the Asp.Net Identity DB even after a pool restart but I see it is not the case at all.
If you have any guidance (or anyone reading this message !) on how to fix this properly I would appreciate it very much.
Best regards !
Hi,
I’ve not hosted ASP.NET Core on IIS as we deploy on Kestrel behind reverse proxy. However I remembered reading something about the token keys which I’ve managed to find. I suspect this is your exact issue. The documentation at https://docs.microsoft.com/en-us/aspnet/core/publishing/iis#data-protection provides details on setting up IIS which I think should help.
Steve
Hi Steve,
THAT is exactly the solution I found after a couple of hours. The App Pool needs to be configured with the Advanced settings.
Now it works flawlessly. Thank you so much for your great help and I hope that many good souls will benefit from this thread exchange.
It took me hours (and hours of stress troubleshooting it in Production !) to make the thing working again !
Cheers and best regards,
J
Steve, by pure curiosity: what is the benefit of deploying on Kestrel behind reverse proxy vs IIS ?
Thanks and regards !
J
For us, it was really the fact that we wanted to run on Linux that meant IIS wasn’t even looked at. We also went for Docker very early on in our system so each of our APIs is self hosted running Kestrel inside the container. That’s the main reason for us.